The receiver of the email initially fell for it, which is understandable given the sophistication of the attempt. She even went as far as to fill in all her payment details such as credit card number AND security code (!), PIN number for ATM card, etc. Fortunately, she got suspicious soon after that. On closer scrutiny the fraud was detected, and she was able to alert the credit card company and the bank before her accounts were raided.
Couldn't happen to you? See for yourself!
Step 1: There's an email in your inbox from 'Amazon Payments':
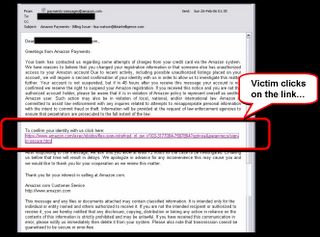
After clicking the link, you land on a fake Amazon.com webpage...
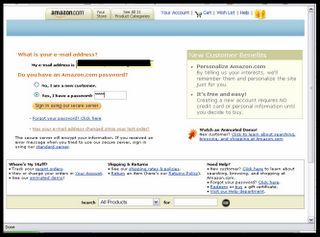
...with an 'amazonaccess.cn' URL, incidentally. Since when is the Amazon Payments Department located in China? But it's easy to overlook, especially since the address structure does include an 'amazon.com' part. Subtle!
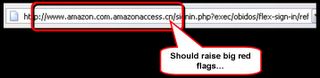
Things are made easy for you. Your email address has been pre-filled...
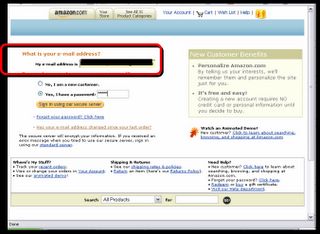
...and also the radio button that says 'Yes, I have a password'!
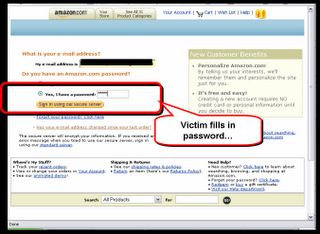
But now for the serious business. What we want, of course, are the credit card details...
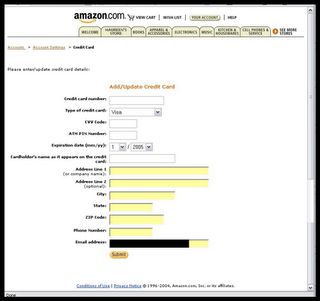
...including your 4-digit credit card security code, and your ATM PIN code! This should raise even bigger red flags than the amazonaccess.cn address.

At this point, the victim might become suspicious and tries to verify by clicking the 'Your Account' tab...
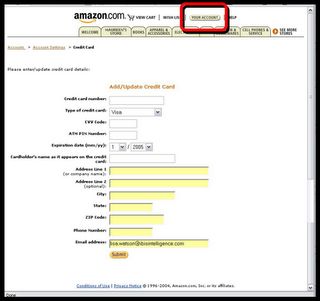
...and guess what? You're directed to the real Amzon.com account page!
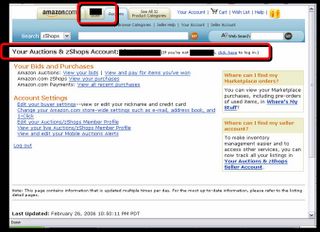
The same happens if you try to verify by clicking on 'Account Settings' in the card data entry page...
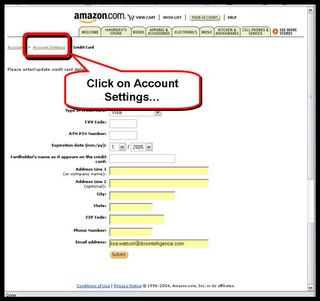
..except that now all of a sudden your account is a 'Seller Account'. Small mistake by the phishers!
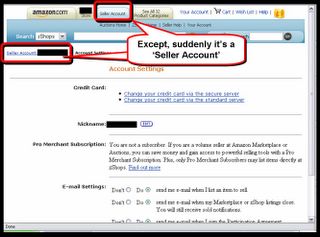
The criminals even foresaw that some suspicious minds would try to log in as a New Customer...
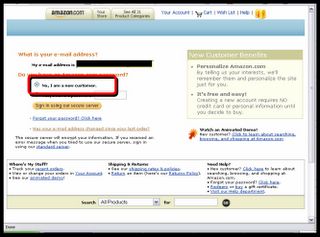
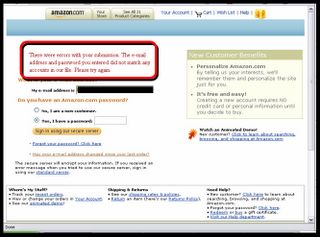
...but we can't have that, of course. After all, one wants to know which credit card and ATM details go with whose name and email address, isn't it? Please try again, dear victim!
Finally, back to the email itself. The criminals have thought of everything - they've even built in a three-day time slot for themselves in which they can plunder your accounts at their leisure. Politely asking for '72 hours for the case to be investigated' should do the trick. It's called 'social engineering'...
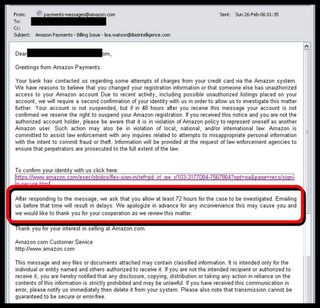
The victim in this case was lucky. She became suspicious and took action before any harm was done. But this little step-by-step makes clear how clever and conniving these phishing scams are set up.
Until Bill Gates or one of his competitors make true on their promises of better security tools and identity protection in the near future (see "Getting there but don't hold your breath") there's only one remedy: stay vigilant.





No comments:
Post a Comment